What I really wanted from disk encryption was ease of use and cross platform portability. I have tried out truecrypt which fits the bill for being cross platform but I found is still a little tedious for use on the desktop (perhaps I'll do another post about my adventures with truecrypt).
Anyhow, LUKS/HAL only just made it into Fedora Core 5 (without much fanfare) and really does make linux disk encryption easy; encrypt your partition, create a file system, plug in your device! The instructions below were based of the how-to from here .
1. Identify the volume you will be encrypting with dmesg. In my case the partition is /dev/sda1 on an external usb2 hard disk which I had previously created with fdisk.
2. Make sure the device is not mounted:
# umount /dev/sda1
3. Create the LUKS partition on the usb drive:
# cryptsetup --verbose --cipher "aes-cbc-essiv:sha256" --key-size 256 -verify-passphrase luksFormat /dev/sda1
Enter and confirm the passphrase for the volume. I suggest using a long passphrase (at least 10 characters, but the more the better obviously!) with a mix of case and numbers.
4. Create a device mapping from the virtual crypto volume to the physical device:
# cryptsetup luksOpen /dev/sda1 usbdisk
This will create a block device /dev/mapper/usbdisk.
5. Make a new file system on our new device:
# mkfs.vfat -v -F 32 -n "20GB USB" /dev/mapper/usbdisk
This will create a FAT32 file system on my external usb disk (I hope to use this with windows too at some point!)
6. Now we just unplug and re-insert the usb disk and:
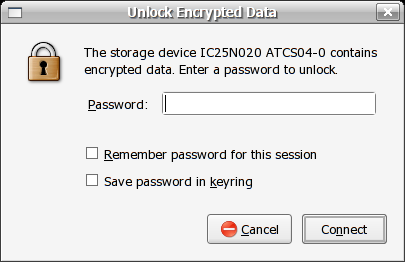
Up pops the password dialogue box for our disk! Enter the passphrase for the volume and the disk will be mounted in /media with a conveniant shortcut on the desktop.
No comments:
Post a Comment